Zero Trust Security Market Size, Share & COVID-19 Impact Analysis, By Application (Network Security, Data Security, Cloud Security, Endpoint Security, and Others), By Authentication Type (Single-factor Authentication and Multi-factor Authentication), By Industry (BFSI, Retail, IT & Telecom, Government, Healthcare, and Others), and Regional Forecast, 2026-2034
Zero Trust Security Market Size
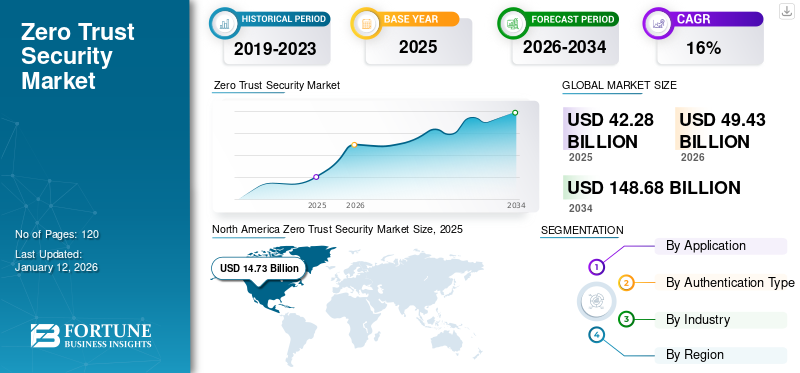
The global zero trust security market size was valued at USD 42.28 billion in 2025 and is projected to grow from USD 49.43 billion in 2026 to USD 148.68 billion by 2034, exhibiting a CAGR of 14.76% during the forecast period. North America dominated the global market with a share of 34.84% in 2025.
Zero trust security (ZTS) is a cybersecurity framework that operates on the principles of not trusting any entity, whether inside or outside the organization’s network, by default. In a zero-trust model, trust is never assumed, and verification is required from everyone and everything trying to connect to resources, regardless of their location or network segment. In addition, continuous monitoring of user and device behavior is essential to detect anomalies and potential security incidents. Thus, growing cyber security concerns among organizations are expected to drive market growth globally in the coming years. ZTS solution is highly preferred in several sectors BFSI, healthcare, retail, government, IT & telecom, and others.
In the scope of work, we have included solutions offered by companies, such as Akamai Technologies, Cisco Systems, Inc., Palo Alto Networks, IBM Corporation, Forcepoint, Broadcom, Zscaler Inc., and others.
Zero Trust Security Market Overview
Market Size:
- 2025: USD 42.28 billion
- 2026: USD 49.43 billion
- 2034 Forecast: USD 148.68 billion
- CAGR (2026–2034): 14.76%
Market Share:
- North America led with 34.84% share in 2025, driven by early adoption across industries and robust implementation strategies.
- BFSI sector held the largest share due to strict regulations and high sensitivity of financial data.
- Healthcare sector is projected to grow at the highest CAGR, fueled by rising demand for secure access in medical systems.
- Network Security segment held the largest share in 2022, while Data Security is expected to grow fastest.
- Single-Factor Authentication accounted for a larger share in 2022, while Multi-Factor Authentication is set to grow at the highest rate.
Industry Trends:
- Broad adoption of zero trust frameworks replacing perimeter-based security with continuous verification models.
- Integration of zero trust with IoT and cloud security to secure hybrid and edge environments.
- Increasing deployments across industries such as retail, government, healthcare, and IT & telecom.
- Acceleration post-COVID, driven by remote work and cloud migration.
Driving Factors:
- Stringent regulatory and data privacy requirements pushing adoption of least-privilege, zero-trust models.
- Rising cyber threats and insider risks increasing the need for advanced security frameworks.
- Rapid cloud migration and hybrid IT expansion requiring consistent access policies across environments.
- Scalability and cost-effectiveness of zero trust architectures helping reduce breach-related costs.
COVID-19 IMPACT
Increased Emphasis on Remote Work Security across Industries amid Pandemic Boosted Market Expansion
With the widespread shift to remote work during the COVID-19 pandemic, organizations faced new challenges in securing distributed networks and endpoints. Zero trust security gained prominence as a model that assumes no implicit trust, even for users inside the corporate network. Moreover, organizations accelerated their migration to cloud services during the pandemic, which led to a surge in cyber threats and attacks. Zero trust principles helped organizations to secure endpoints by implementing robust controls, continuous monitoring, and dynamic access policies based on user behavior. Further, with increased reliance on collaboration tools for remote work, securing communication channels became a priority. ZTS principles extend to securing collaboration platforms and ensuring secure communication and data sharing. These factors fueled the zero trust security market growth during the pandemic.
Zero Trust Security Market Trends
Rapid Adoption of Zero Trust Framework to Fuel Market Growth
Organizations across various industries are increasingly adopting the zero trust security framework as a fundamental approach to cybersecurity. The need for continuous and adaptive security in dynamic IT environments drives the paradigm shift from traditional perimeter-based models to a zero-trust model.
With the proliferation of Internet of Things (IoT) devices, there is a growing trend toward implementing ZTS for IoT. This involves applying zero-trust principles to secure the interactions and communications between IoT devices and the broader network. Moreover, these principles are being integrated with cloud security strategies. As organizations migrate their operations to the cloud, the combination of zero trust and cloud security measures ensures consistent and secure access to resources across on-premises and cloud environments. These aforementioned factors contribute to market growth.
Download Free sample to learn more about this report.
Zero Trust Security Market Growth Factors
Increasing Regulatory Compliance Requirements and Data Privacy Concerns Augment Market Growth
Stringent data protection regulations and compliance requirements drive organizations to implement robust security measures. ZTS aligns with regulatory mandates by ensuring secure access controls and data protection. In addition, growing concerns about data privacy and the need to protect sensitive information propel the adoption of ZTS solutions. The model ensures that access to critical data is strictly controlled, reducing the risk of unauthorized data exposure. As per industry experts, IoT-connected devices are expected to increase to USD 43 billion by 2023. Thus, the continuous innovation by zero trust security vendors in providing comprehensive zero trust solutions contributes to market growth.
RESTRAINING FACTORS
Complex Implementation Process of ZTS Solutions May Hinder Market Expansion
Implementing a ZTS model can be complex and challenging. Organizations often need to reconfigure existing network architectures, redefine access policies, and deploy new security technologies. Retrofitting older systems to align with zero trust principles can be resource-intensive and may require significant investments. Moreover, shifting to a zero-trust model often requires changes in user behavior and access patterns. Employees and users may resist the additional authentication steps and stricter access controls, necessitating effective change management strategies.
In addition, integrating ZTS with existing security solutions, such as firewalls, security information and event management (SIEM) tools, can be challenging. Ensuring seamless collaboration between different security components is crucial for a comprehensive security posture. Thus, the presence of various complexities in the implementation process of ZTS solutions in organizations' existing network infrastructure may restrain market growth.
Zero Trust Security Market Segmentation Analysis
By Application Analysis
Continuous Verification of Remote Access Enhances Network Security Segment Growth
Based on application, the market is classified into network security, data security, cloud security, endpoint security, and others (application security).
The network security segment secured the maximum share of the market in 2022 owing to its ability to constantly engage in the verification of user identities and devices attempting to access resources. Users and devices are not trusted by default. Further, as remote work becomes prevalent, ZTS is crucial for securing remote access to network resources. The cloud security segment is projected to dominate the market with a share of 26.5% in 2026.
The data security segment is set to rise at the highest CAGR in the coming years as it promotes the use of encryption for data in transit and at rest. Secure communication channels and encrypted storage methods safeguard sensitive data, preventing unauthorized access even if intercepted. Moreover, Data Loss Prevention (DLP) can be integrated into a ZTS framework to monitor and prevent unauthorized data exfiltration.
By Authentication Type Analysis
Simplicity and User Experience Among Businesses to Propel the Adoption of Single-factor Authentication
Based on authentication type, the market is bifurcated into single-factor authentication and multi-factor authentication.
The single-factor authentication segment held a larger share of the market in 2022, as it is a simpler and user-friendly method. In certain scenarios, organizations might adopt this method as a temporary or transitional measure while moving toward a more comprehensive ZTS model. This allows for a phased approach to security enhancement.
The multi-factor authentication segment is expected to grow at the utmost CAGR during the forecast period. Multi-factor authentication requires users to provide multiple forms of authentication, usually something they know, such as a password and something they have, such as a mobile device. This enhances identity verification, reducing the risk of unauthorized access. Even if attackers obtain one authentication factor, they would need additional factors to gain access. Thus, a rise in demand for multi-factor authentication is expected to fuel market growth. The Multi-factor Authentication segment is projected to dominate the market with a share of 52.59% in 2026.
By Industry Analysis
To know how our report can help streamline your business, Speak to Analyst
Growing Demand for Continuous Verification of Identities in BFSI to Foster Segment Growth
Based on industry, the market is segmented into BFSI, healthcare, retail, government, IT & telecom, and others (energy & utilities).
The BFSI sector held the maximum zero trust security market share in 2022. ZTS requires continuous verification of user identities. In BFSI, this means ensuring that only authenticated and authorized individuals have access to sensitive financial data, applications, and systems. Moreover, in BFSI, the confidentiality of financial transactions is paramount, and the use of ZTS software plays a vital role in safeguarding sensitive information from attackers. The BFSI segment is expected to lead the market, contributing 25.11% globally in 2026.
The healthcare sector is predicted to rise at the highest CAGR over the projected period. In healthcare, it ensures that only authenticated and authorized individuals, such as healthcare professionals and staff, have access to patient records and critical healthcare systems. Moreover, the implementation of ZTS solutions in healthcare ensures that security measures align with the specific needs and workflows of healthcare providers without disrupting critical operations.
REGIONAL INSIGHTS
Geographically, the market is studied across North America, Europe, Asia Pacific, South America, and the Middle East & Africa.
North America
North America Zero Trust Security Market Size, 2025
To get more information on the regional analysis of this market, Download Free sample
North America holds the largest share in this market. Implementing network micro-segmentation is a key component of ZTS in North America. By dividing networks into smaller segments, organizations limit the lateral movement of threats and contain potential breaches more effectively. Moreover, organizations in the U.S. are increasingly adopting cloud services, and ZTS aligns with cloud security strategies. It ensures that security measures extend seamlessly to cloud environments, preventing unauthorized access to cloud-based resources. The U.S. market is estimated to reach USD 11.37 billion by 2026.
Asia Pacific
To know how our report can help streamline your business, Speak to Analyst
In Asia Pacific, organizations are majorly adopting access controls based on contextual factors, such as behavior, location, and device health. This adaptability is crucial for maintaining security in a constantly changing threat landscape. In addition, different industries in Asia Pacific, including finance, healthcare, and government, have embraced zero trust security to address industry-specific challenges and regulatory requirements. This sector-specific adoption ensures tailored security measures. All these factors are expected to fuel the regional growth during the forecast period. The Japan market is forecast to reach USD 2.76 billion by 2026. The China market is poised to reach USD 3.38 billion by 2026. The India market is set to reach USD 2.47 billion by 2026.
Europe
Europe is subject to stringent data privacy regulations, such as the General Data Protection Regulation (GDPR). ZTS aligns with GDPR requirements by enforcing strict access controls and protecting sensitive data, contributing to compliance efforts. The dynamic nature of cyber threats has led organizations in Europe to adopt zero trust security as a proactive defense mechanism. Continuous verification and adaptive access controls help protect against evolving and sophisticated cyberattacks. The UK market is expected to reach USD 2.28 billion by 2026. The Germany market is anticipated to reach USD 2.24 billion by 2026.
Middle East & Africa
The increased prevalence of remote work in the Middle East & Africa has emphasized the need for secure remote access. Zero trust security ensures that users connecting from various locations undergo continuous verification. Moreover, it extends to managing access for vendors and third parties in South America. Organizations recognize the importance of implementing stringent controls to secure access for external entities, minimizing potential risks associated with third-party access. These factors play a vital role in the significant growth of the market in the region.
KEY INDUSTRY PLAYERS
Players Focus on Introducing Novel Products to Increase Their Consumer Base
Some of the top zero trust security companies are Akamai Technologies, Cisco Systems, Inc., Palo Alto Networks, and Zscalar, Inc. These market players are concentrating on expanding their geographical presence across the globe by presenting industry-specific services. Leading companies are emphasizing acquisitions and collaborations with regional players strategically to maintain dominance across regions. Top market participants are introducing novel products to increase their consumer base. An increase in constant R&D investments for product innovations is enhancing market expansion. Hence, top companies are rapidly implementing these strategic initiatives to sustain their competitiveness in the market.
List of Top Zero Trust Security Companies:
- Akamai Technologies (U.S.)
- Cisco Systems, Inc. (U.S.)
- Palo Alto Networks (U.S.)
- IBM Corporation (U.S.)
- Zscalar, Inc. (U.S.)
- Broadcom (U.S.)
- CrowdStrike (U.S.)
- Forcepoint (U.S.)
- Skyhigh Security (Musarubra US LLC) (U.S.)
- Check Point Software Technologies (Israel)
KEY INDUSTRY DEVELOPMENTS:
- November 2023: Palo Alto Networks launched Strata Cloud Manager, an AI-powered Zero Trust management solution. This solution is expected to protect consumers’ data with the combination of Artificial Intelligence (AI) technology and the Zero Trust method.
- September 2023: Zscalar, Inc. partnered with CrowdStrike and Imprivata to provide a zero-trust cyber security solution for medical institutions. Zscaler integrated its ZTS solution with the Imprivata Digital Identity Platform to provide threat protection for multiple healthcare devices.
- August 2023: Akamai Technologies engaged in a new partnership with Secureworks, the U.S.-based cybersecurity solution provider. This partnership provides security operation teams with the data and intelligence required to scale secure access from any remote location.
- May 2023: Zscaler, Inc. engaged in a partnership with Center for Internet Security, Inc. (CIS), a non-profit cybersecurity organization. Through this partnership, Zscalar aims to advance cybersecurity for State, Local, Tribal and Territorial (SLTT) governments.
- May 2023: Palo Alto Networks extended its partnership with Wipro to provide customers with a zero trust security solution. The company combined its Next-Generation Security Platform with Wipro's Security and Infrastructure Services to help organizations protect critical assets.
REPORT COVERAGE
The report provides a detailed market analysis and focuses on key aspects such as leading companies, product/service types, and leading applications of the product. Besides this, it offers insights into the market trends and highlights key industry developments. In addition to the factors above, the report encompasses several factors that have contributed to the growth of the market in recent years.
Request for Customization to gain extensive market insights.
Report Scope & Segmentation
|
ATTRIBUTE |
DETAILS |
|
Study Period |
2021-2034 |
|
Base Year |
2025 |
|
Forecast Period |
2026-2034 |
|
Historical Period |
2021-2024 |
|
Growth Rate |
CAGR of 14.76% from 2026 to 2034 |
|
Unit |
Value (USD Billion) |
|
Segmentation |
By Application
By Authentication Type
By Industry
By Region
|
Frequently Asked Questions
A study by Fortune Business Insights Inc. says that the market is projected to reach USD 148.68 billion by 2034.
In 2025, the market stood at USD 42.28 billion.
The market is projected to grow at a CAGR of 14.76% during the forecast period.
By application, the network security segment leads the market.
Increasing regulatory compliance requirements and data privacy concerns augment market growth.
Akamai Technologies, Cisco Systems, Inc., Palo Alto Networks, IBM Corporation, Forcepoint, Zscaler Inc., and others are the top players in the market.
North America holds the largest market with a share of 34.84% in 2025.
By industry, the healthcare segment is expected to grow at the highest CAGR during the forecast period.
Related Reports
-
US +1 833 909 2966 ( Toll Free )
-
Get In Touch With Us